Networkforensic
Threat hunting
Wireshark forensic profiles and tools
I build my own profiles for Wireshark when I need to get more logic out of Wireshark, Some of these profiles are published here for anyone to use. It will speed things up, when you analyse differet kinds of traffic. The profiles can be used on all OS type systems where Wireshark can run.
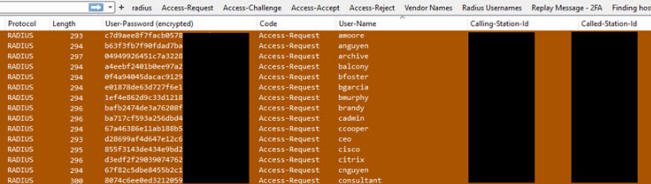
Radius
Related to all the fuss about
Blast Radius
attacks. I had to build a profile for Wireshark that gave me more
logic to into the Radius protocoll. With this I found a lot of
Brute-force attacks originating from Russian IP's. Something you
easily will miss with normal default profiles for Wireshark. You can
also spot 2FA auth with this and a lot more.
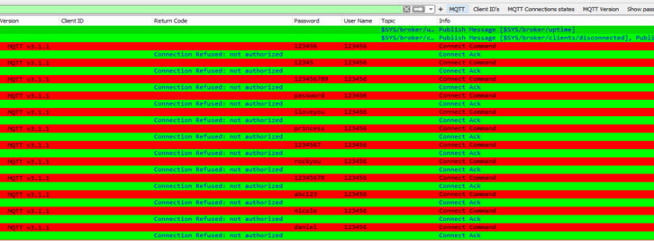
MQTT
MQTT is a communication protocol with features specifically targeted
at IoT solutions. It is also used by APT groups as C&C for malware.
I have made some basic filters for analysis of the MQTT traffic. The
below sample is based on a brute force attacks.
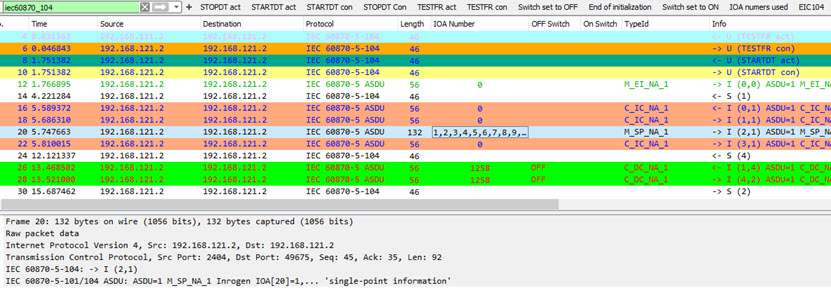
IEC-104
IEC-104 is a transmission protocols used for things like
controlling a powergrid.
When analysing this protocol i can recommend the documentation
TR-IEC104. Be aware that
Wireshark do not interpet all element types. So this is the best it
can be for now.
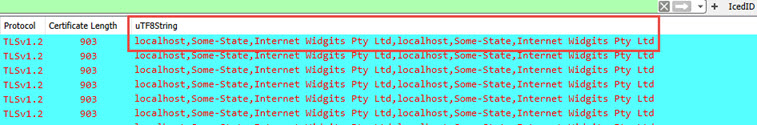
IcedID TLS Inspection
Hunting for the malware framework IcedID it is nessary to look for
what names a certificate was issued with. Quite often it it a self
signed certificate with bogus names. like this on with the name
"localhost".
GQUIC
or QUIC Profile (Updated 21-11-2023)
Looking for information about QUIC ore GQUIC. The newest protocol
schould only be QUIC and was released in 2021 v.1. - GQUIC is
obsolete.
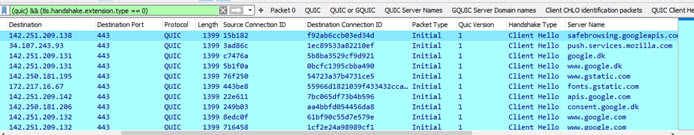
ICMP Profile
Hunting for ICMP tunneling is quite easy with this Wireshark
profile. Exampel of a pTunnel running below.
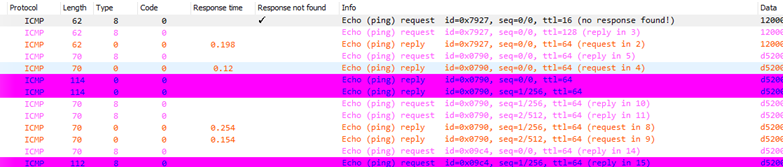
iSCSI
profile
Hunting for iSCSI auth traffic and authentications. Easy to spot
with this profile
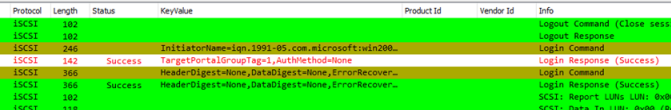
DHCP Profile (Updated 03-01-2021)
Often you will hunt for a rough DHCP server placed on your network.
This profile will make this very easy.
Optimized for Wiresharek 3.x versions.
DNS Profile
This will make DNS identification easy and bring DNS traffic to life
in Wireshark
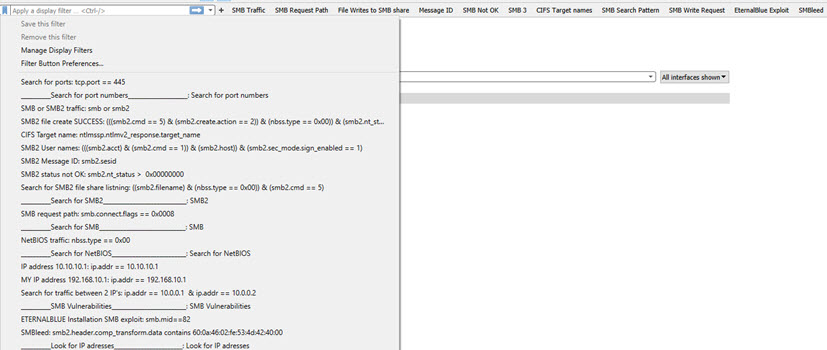
SMB Profile
(Many updates for this profile as of 02-01-2020)
This will bring the analysis of SMB, SMB2 and SMB3 network traffic
to life in Wireshark. What you typically is looking for, is right
there...
More information about MS implementation
here
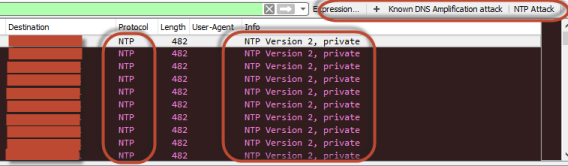
DDOS profile
(Updated 03-03-2022)
Based on my work for an ISP and the manage of Advanced DDOS
mitigation. This is based on known DDOS attacks. You can analyze the
type of attack quite fast. Tested
Wireshark V2.6.3
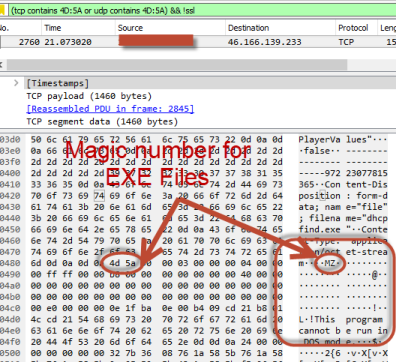
Magic numbers profile
Based on file types and there magic numbers it is easy to look for
different file types in network traffic like exe files and so on,
hidden in network traffic. Tested Wireshark
V2.6.3
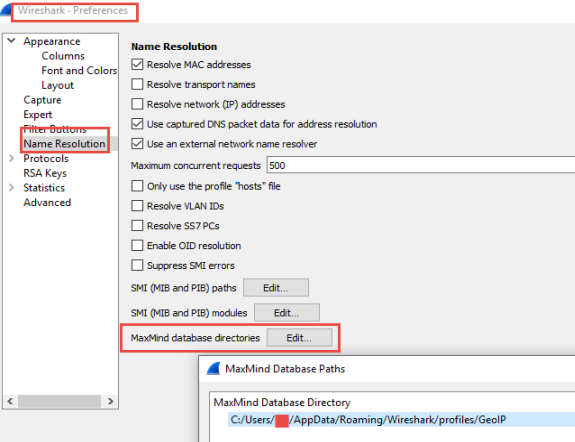
Geolite2 databases for Wireshark
Wireshark can do name resolution on
captured traffic.
To get the free updated
Maxmind databases you need to sign up for a profile first.
(please do so)
You can get an older Maxmind databease
from here.

Tools
ColarSoft Packet Replay
Colarsoft Packet Builder
Caploader
Moloch
Network Miner
Security Onion
SNORT IDS/IPS
SOF-ELK
SplitCap
Suricata IDS/IPS
TraceWrangler
Wazuh
Wireshark
Zeek
Forensic
report
Report
framework
Cheat
Sheets
Port numbers
IPv4 Subnetting
Network Forensics and Analysis Poster
Poster Find
Evidence
Poster Find Evil
Scapy
Security Onion
Sysmon
Tcpdump
VOIP Basics
Wireshark
Display Filters
Tips
BPF
Filter syntax
Enum
Kibana
Netsh
Trace
Nmap
nping
Nslookup SPF
OS
TTL Fingerprint
Port list
PowerShell Commands
Local LAN NET
bloks
SID
SMTP Relay
Tjek
Google Tips
T-Shark
USB Boot Disk
Wireshark
Blacknurse Attack
Blacknurse.dk
Netresec
Wikipedia
PDF File